Configure Instances Internet Access
Please read Workshops Organisation if you haven’t done so.
If you are attending a workshop using a Cloud-SPAN AWS account, you don’t need to complete this episode.
If you are self-studying the course or attending a workshop using your AWS account, you must complete this episode and for that you will need:
to have created and configured your AWS account as described in the episodes Create Your AWS Account and Configure Your AWS Account.
the AWS Console login details of your IAM user account: login page, username and password.
Overview
These are the main steps you will follow to configure internet access for the instances you will create with the Scripts:
Create Your Base Domain Name.
This step is optional. If you decide not to create a base domain name, or do not specify it (as described in the next episode) when creating instances, the instances created by the Scripts will be accessed (logged in) using the IP addresses allocated to the instancs by AWS.
If you decide to create a base domain name, and specify it (as described in the next episode) when creating instances, the Scripts will create a sub-domain to access each instance. If you are using an AWS institutional account, your base domain name may itself be a sub-domain within a domain name managed by your institution. Check the callout at the end of this section to ensure your based domain name is properly configured by you or your IT department.Create Your AWS Security Group.
An AWS security group is a set of rules to configure the Internet communication ports of AWS instances. The security group you will create will enable the communication port used by thesshprogram. We only need one security group as all instances need the same configuration. If you are using an AWS institutional account, you should not have any problem creating a security group — try to create it; if you cannot then contact your IT deparment.Select an AWS Subnet to Access the Instances.
An AWS subnet is a network within an AWS region to which the instances created by the Scripts will be connected so that they can be accessed from anywhere.
This step is optional. If you do not specify a subnet-id (as described in the next episode) when creating instances, the Scripts will try to obtain a subnet-id from your AWS account. We have successfully tested the Scripts to obtain and use a subnet-id running the scripts with a personal AWS account and with an institutional AWS account. The personal account was configured to use the default subnets allocated by AWS. The institutional account was configured not to use the default subnets allocated by AWS, but other subnets configured by the IT department of our institution.
If the scripts cannot obtain a subnet-id, they will display a message describing how to obtain a subnet-id (see below the detailed instructions for this step): to search for vpc (virtual private cloud) in the AWS Console (in the search box at the top), then click on subnets on the left menu, and to copy one of the subnet-id’s displayed. NB: if no subnet-id is displayed in the AWS Console, and you are using an AWS institutional account, you will need to contact your IT department.
You must do the above steps using the AWS Console with your IAM user account. These are the instructions to login to your IAM account:
- Open a new browser window and enter the address of the login page for your account IAM users. The address contains your account alias or your 12-digit account number and has this form:
- https://youraccountalias.signin.aws.amazon.com/console
- https://123456789012.signin.aws.amazon.com/console
- Enter your IAM username and password. You may also get a Security check to complete.
- Set the region to Ireland (eu-west-1) if it is not, by clicking on the drop-down menu at the top to the right, see top right on the page below.
1. Create Your Base Domain Name
Go to the Route 53 Dashboard
You are now logged in to your IAM account. To create your base domain name, type route 53 in the AWS search box at the top and press Enter.
You will be presented with the “Route 53 Dashboard”. Click on Register domain.
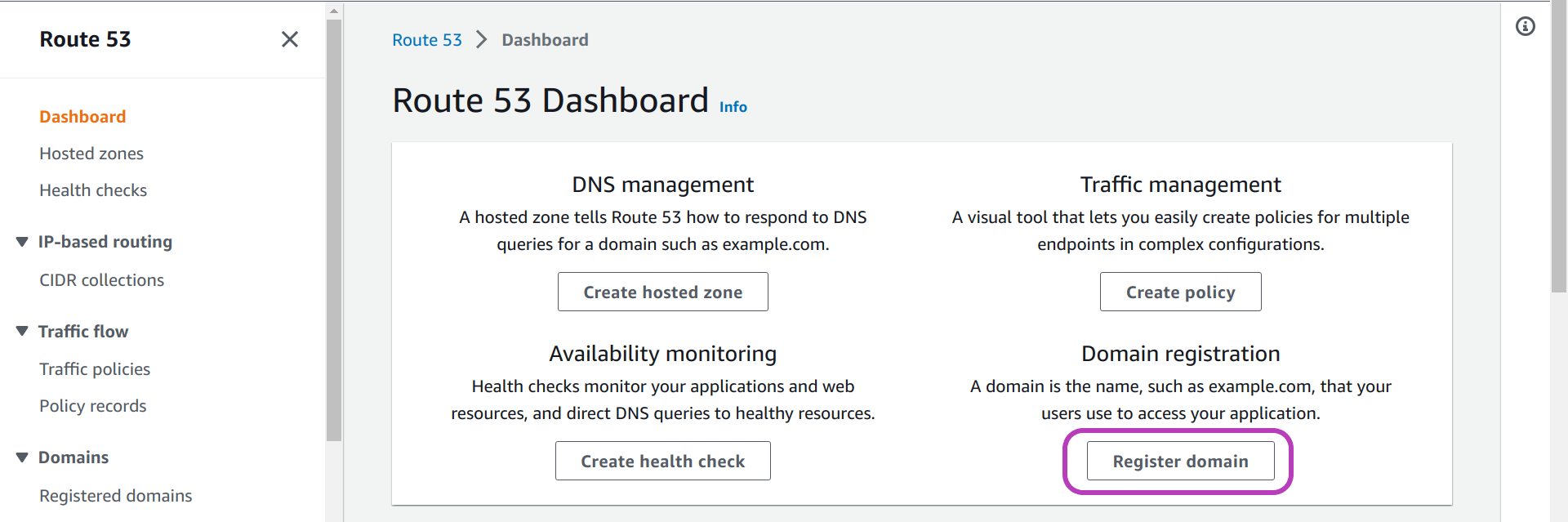
Choose your domain name
On the page that appears, “Choose a domain name”, you are going to:
- type your base domain name —
awsplaicloudis our domain name in the page below.- You cannot use dots (.) but you can use hyphens or minus signs (-) to link a few words, for example:
cloud-spanorcloud-span-2023.
- You cannot use dots (.) but you can use hyphens or minus signs (-) to link a few words, for example:
- click on “.com -$12.00” drop-down menu to choose a top level domain (TLD) —
.comwas our choice.
- The cheapest TLD in AWS Route 53 is
.linkat US $5.00 per one year.
- The cheapest TLD in AWS Route 53 is
- click Check to check for the availability of your domain name and TLD.
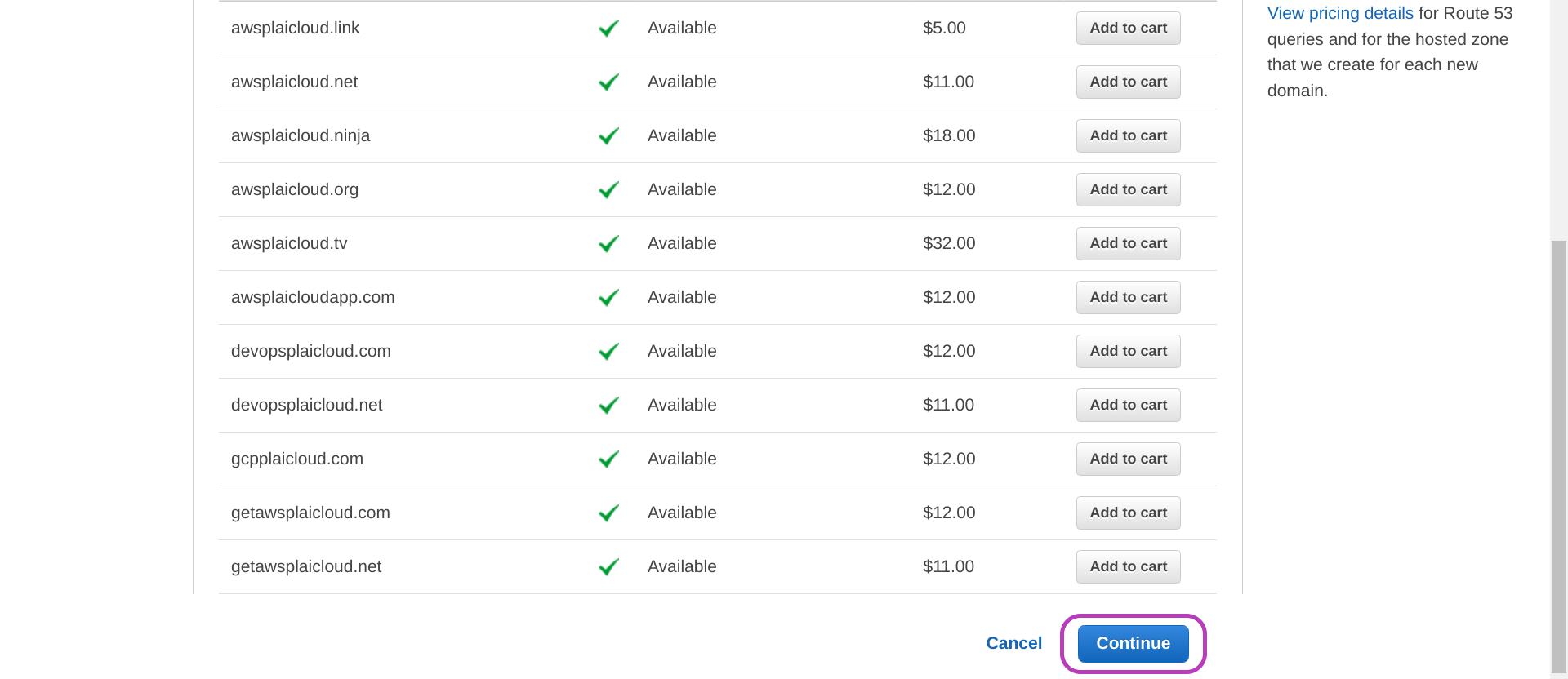
- You will be presented with the Availability for your-domain-name and a list of Related domain suggestions.
- click the Add to cart button to the right of the domain name that you want to create (buy).
- In the page, we have already clicked on the button to the right of
awsplaicloud.comwhich hence appears on the Shopping cart (top right).
- In the page, we have already clicked on the button to the right of
- scroll down and click Continue.
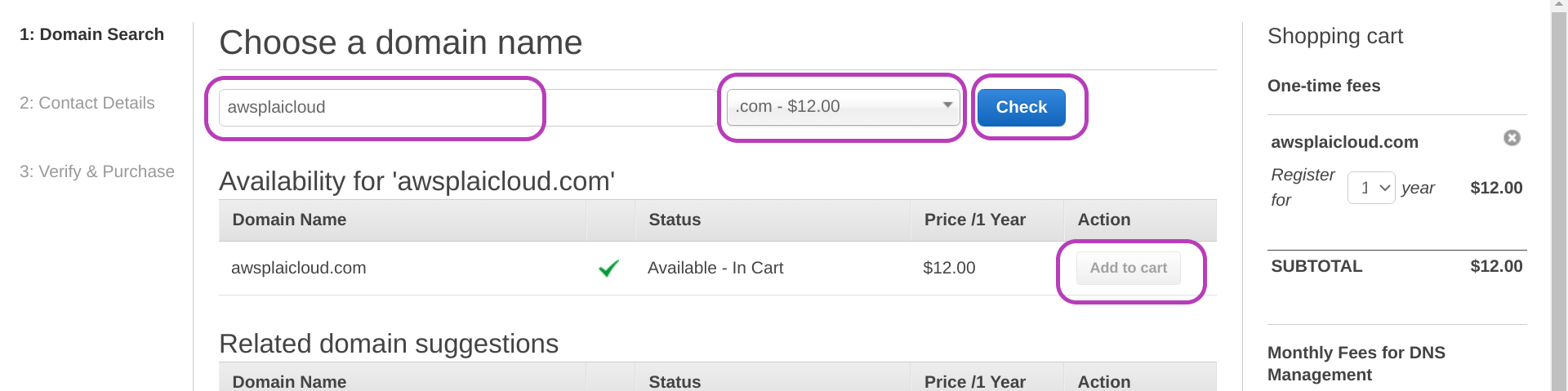
Enter the contact details for your domain
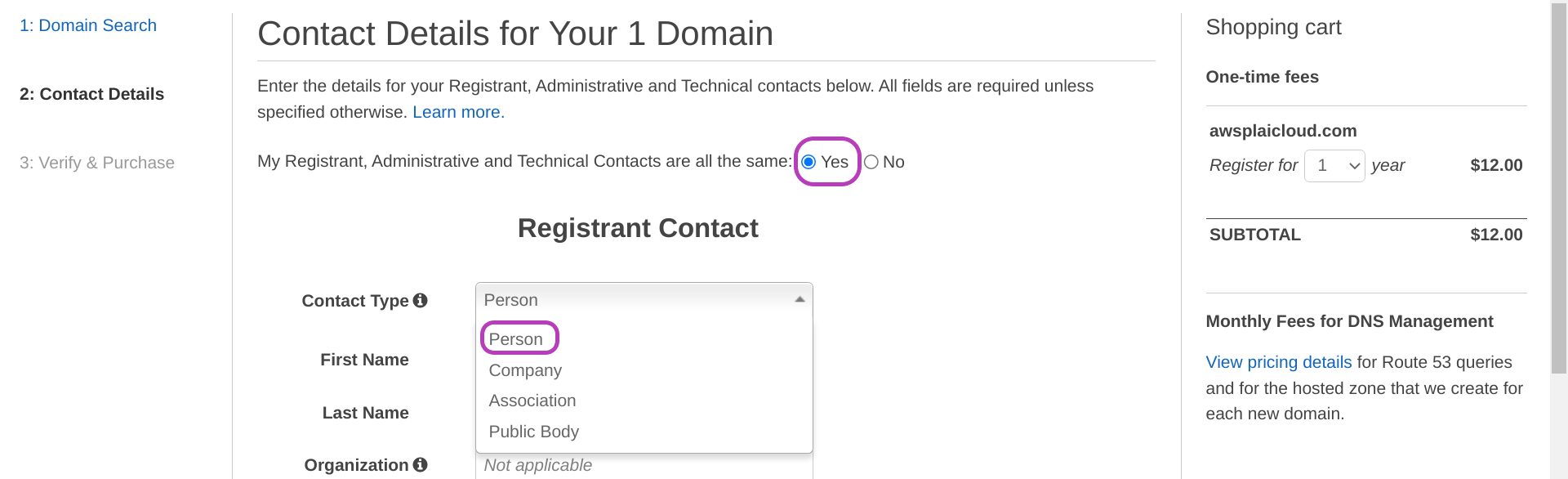
You will now be presented with the page “Contact Details for Your 1 Domain”. Do as follows in this page:
- select Yes for “My Registrant, Administrative and Technical Contacts are all the same”.
- select Person for “Contact Type”.
- enter your contact details.
- scroll down and select Enable for “Privacy Protection”.
- click Continue.
Check your contact details and complete order
In the page that appears, “Check your contact details” (not shown below), you will see at the top the contact details for your Registrant Contact, Administrative Contact and Technical Contact — our contacts are not shown.
Scroll down until you see options shown below.
- select Disable for “Do you want to automatically renew your domain?”. If you select Enable, your domain name registration will be renewed every year which will incur the same or slightly higher cost every year. You can disable this option later if you prefer.
- check the box next to “I have read and agree to the AWS Domain Name Registration Agreement”.
- click Complete Order.
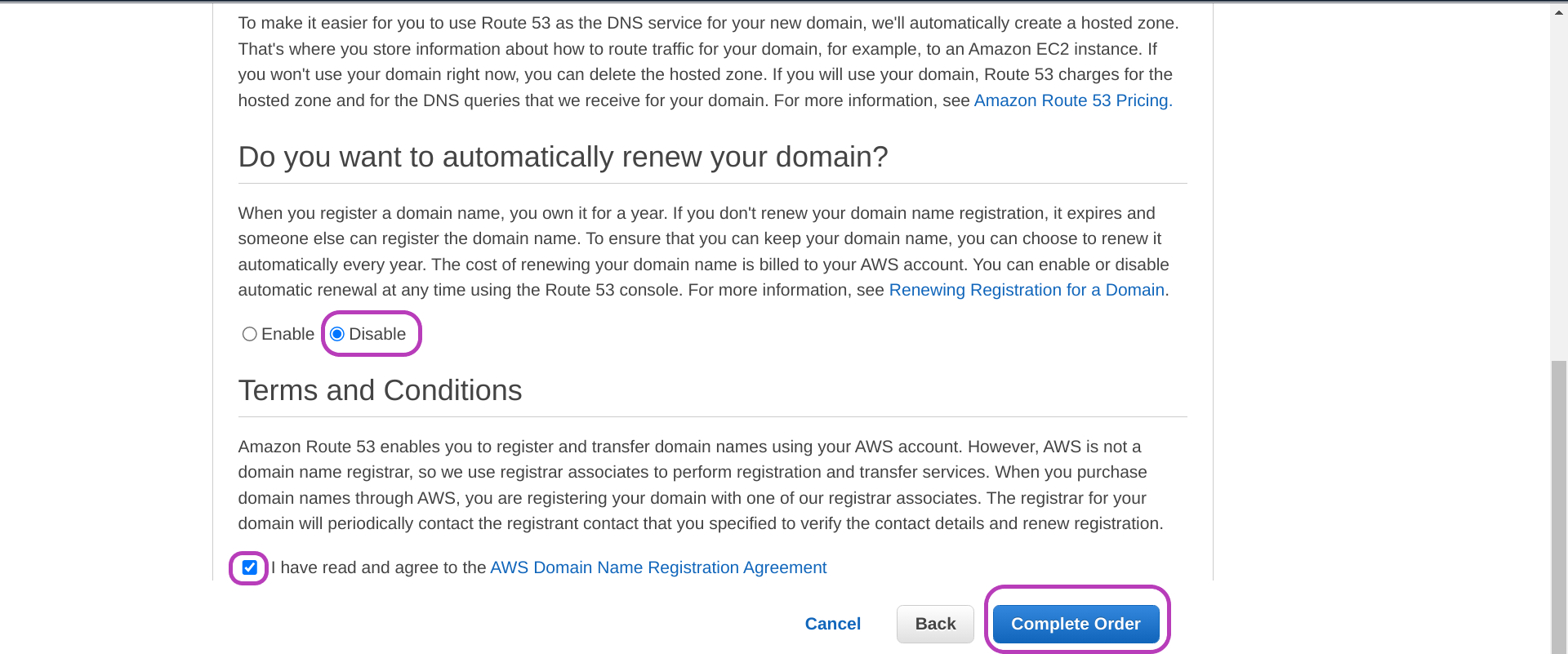
You will then be presented with the page below. First click Close and then Hosted zones on the left pane.
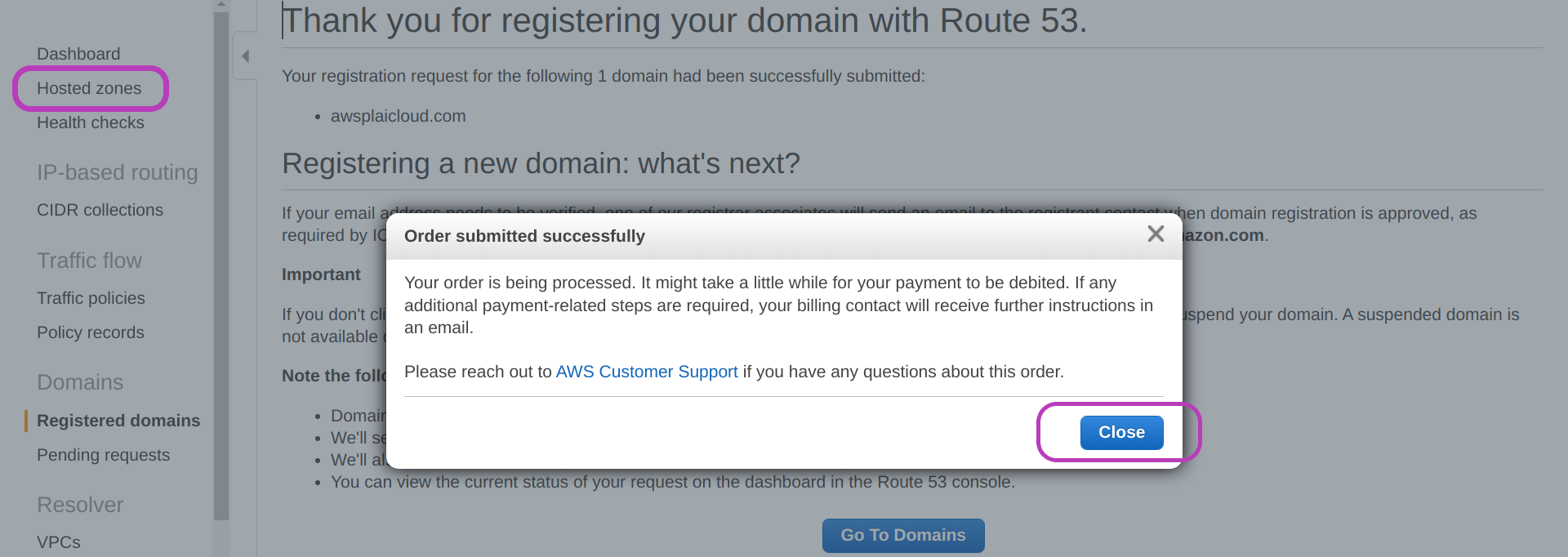
Make a note of your host zone name (domain name) and host zone id
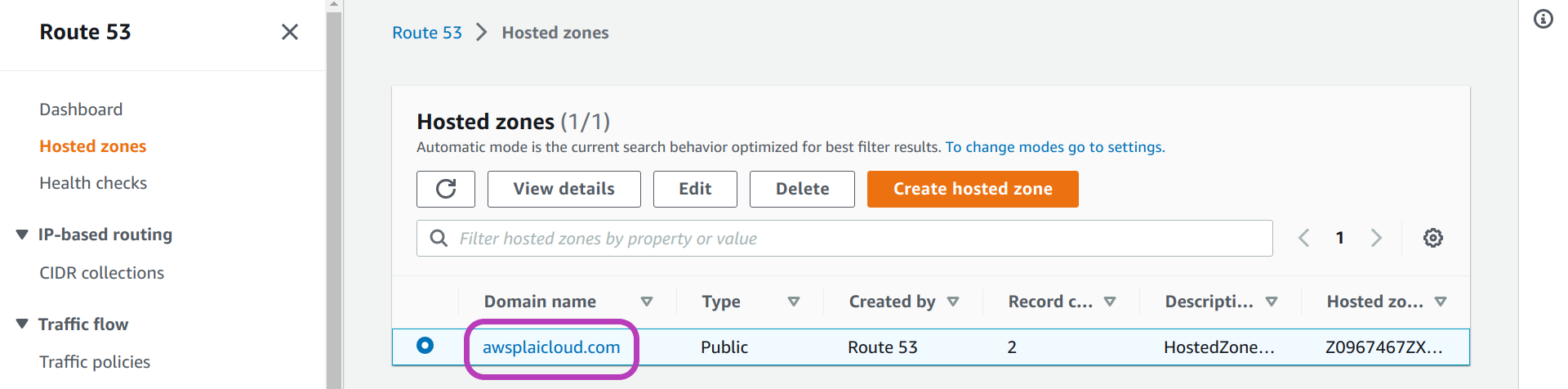
In the page that appears, “Hosted zones”, your domain name should be listed as shown in the page below for our domain name awsplaicloud.com.
However, it may take a few (2-3) minutes for your domain name to be registered and hence to appear in the domain name list.
Refresh the page every now and then until your domain name appears. Then click “your-domain-name” (awsplaicloud.com).
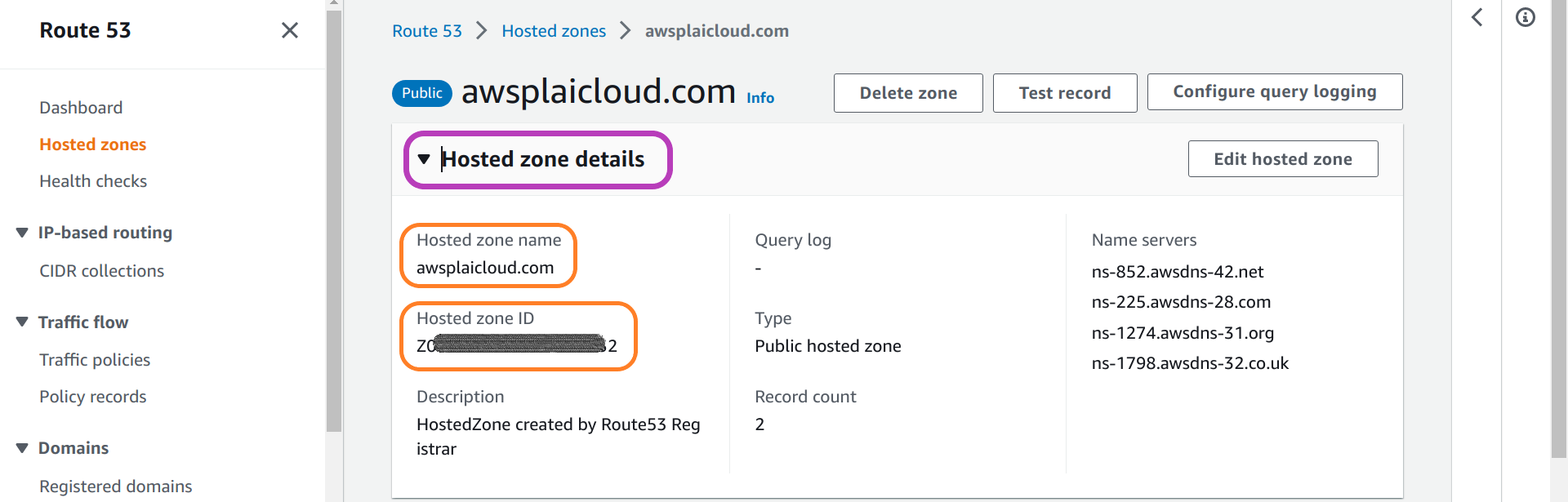
In the page that appears, “your-domain-name”, click Hosted zone details, and from the details that will be displayed, make a note of both the Hosted zone name (your domain name) and the Hosted zone ID (concealed in dark grey below), as you will use them later to configure the Scripts.
Recall that the base domain name awsplaicloud.com was created with an AWS personal account and that instances domain names will have the form instancename-001.awsplaicloud.com, where instancename-001 will be a subdomain name within awsplaicloudcom.
Using an AWS institutional account, your base domain name will likely be something like cloud-span.aws.york.ac.uk, and instances domain names will have the form instancename-001.cloud-span.aws.york.ac.uk, where:
york.ac.ukis the base domain name of the University of York, and has two parts: the domain name per se,york, and the domain suffix or top-level domain (TLD),ac.uk, which must be chosen among various other suffixes such as:.com,.edu,.net,.org,.link, etc.awsis a subdomain managed by the IT department to identify AWS domains used by a department or project within the university — similar subdomains aregcpfor Google Cloud Platform, andazurefor Microsoft cloud platform.cloud-spanis the subdomain configured by the IT department for the Cloud-SPAN project. Note that words separated by a hyphen (-) count as a single word in domain and subdomain names. It is the dot.that separates a domain name into subdomains, though some subdomains pairs are handled as one, for example:co.ukis handled as one TLD by AWS and probably by other providers of domain names.instancename-001is the subdomain for the instance-001 created by the Scripts.- IMPORTANT: while both
cloud-spanandinstancename-001are both subdomains (respectively withinaws.york.ac.ukandcloud-span.aws.york.ac.uk), they are configured differently:cloud-spanis configured as a host zone (asawsplaicloud.comwas configured above), and hence has an AWS host zone id. You need to configure, or ask your IT department to configure, your base domain name as a host zone so you can configure the Scripts with the corresponding host zone name and host zone id.instancename-001,instancename-002..,instancename-999are configured by the Scripts as A Records (which map domain names to IPv4 addresses) within the specified host zone.
2. Create Your AWS Security Group
Create and name your security group
On the page that appears, “Security Groups”, click Create security group — ignore the default security group if it is listed.
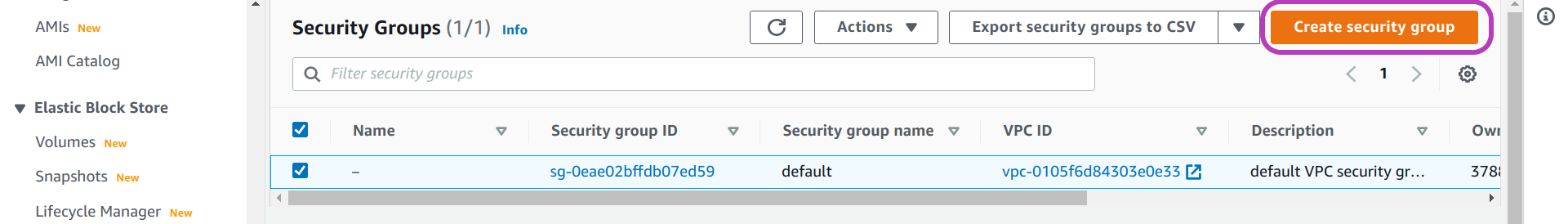
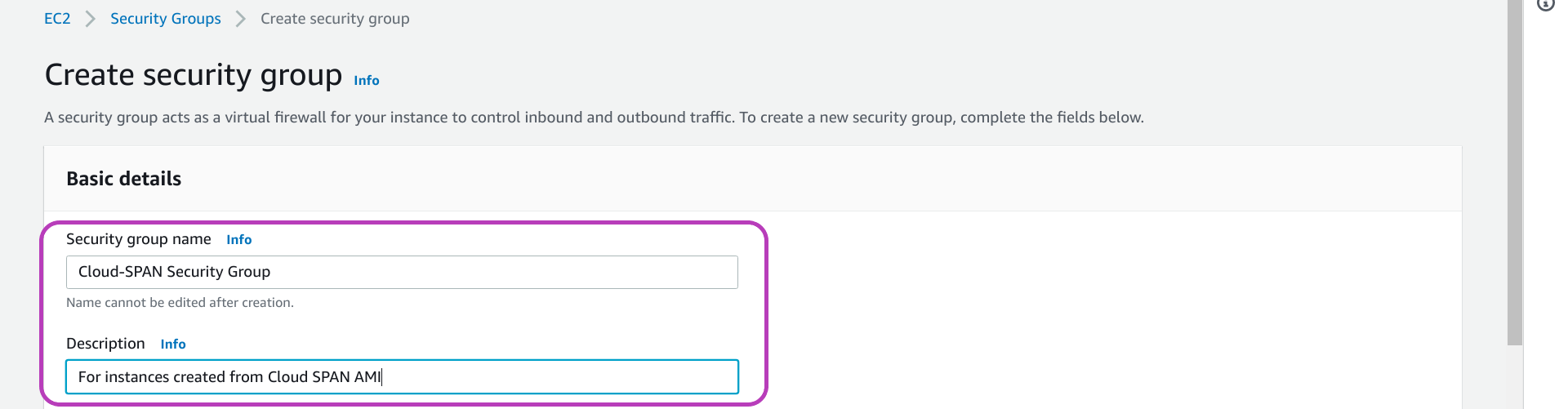
You will be presented with the page “Create security group”. In this page you are going to type a name and a description for your security group, as shown below:
Create the inbound rules for your security group
Now scroll down the page until you see the heading Inbound rules:
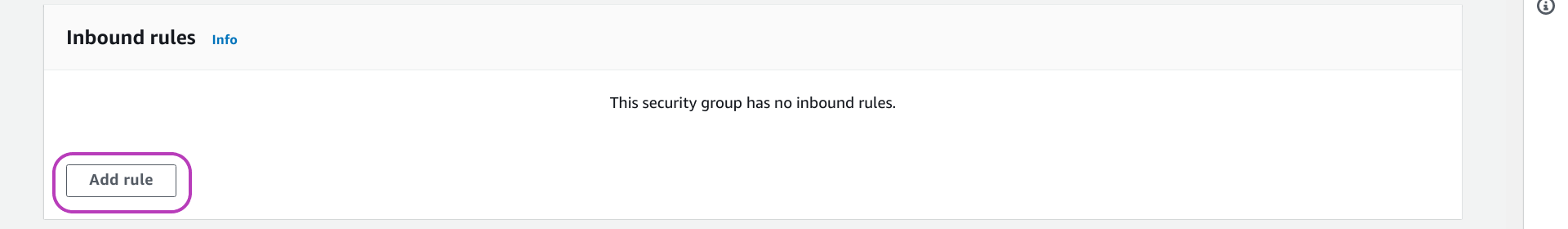
We are going to specify for inbound rules:
- Click the Add rule button four times so that four rows appear.
- On the left column (labelled Type), select SSH for rows 1 and 2 and Custom TCP for rows 3 and 4.
- On the third column (labelled Port range) enter the number 8787 on rows 3 and 4.
- On the fourth column (labelled Source), select Anywhere-IPv4 for rows 1 and 3 and Anywhere-IPv6 for rows 2 and 4.
The first four columns of the table should now look like this:
| Type | Protocol | Port Range | Source |
|---|---|---|---|
| SSH | TCP | 22 | Anywhere-IPv4 |
| SSH | TCP | 22 | Anywhere-IPv6 |
| Custom TCP | TCP | 8787 | Anywhere-IPv4 |
| Custom TCP | TCP | 8787 | Anywhere-IPv6 |
There is no need to define outbound rules nor tags.
Scroll down to the end of the page and click Create security group.
Make a note of your security group id
You should now see a page like the one below showing the details of your security group including the inbound rules you created. Make a note of your security group id at the top (concealed in dark grey in the page below), as you will use it later to configure the Scripts.
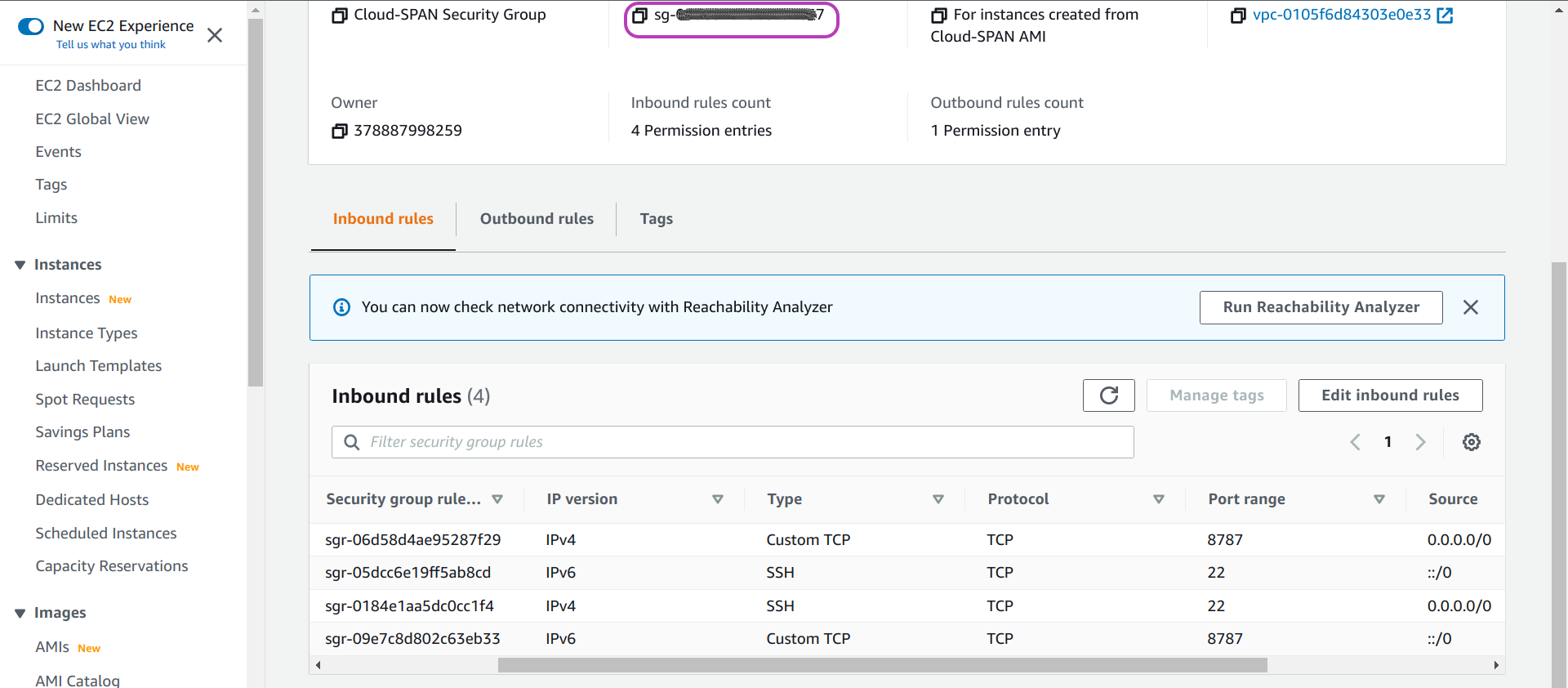
3. Select an AWS Subnet to Access the Instances
Go to the Virtual Private Cloud (VPC) Dashboard
To select an AWS Subnet, type vpc in the AWS search box at the top and press Enter. Check that you are in the Ireland region and set it thus if not.
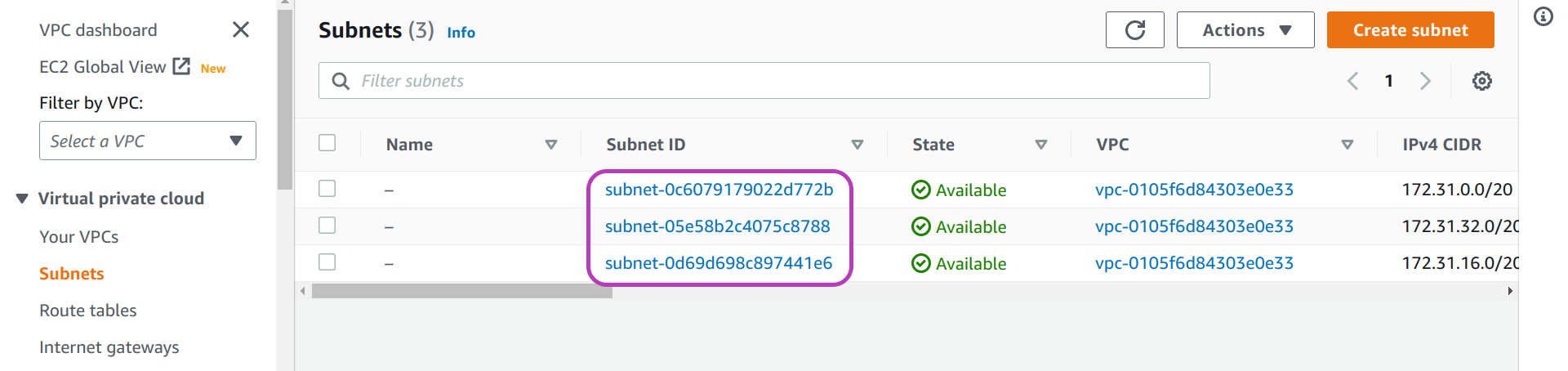
You will be presented with the “VPC Dashboard”. Click Subnets.
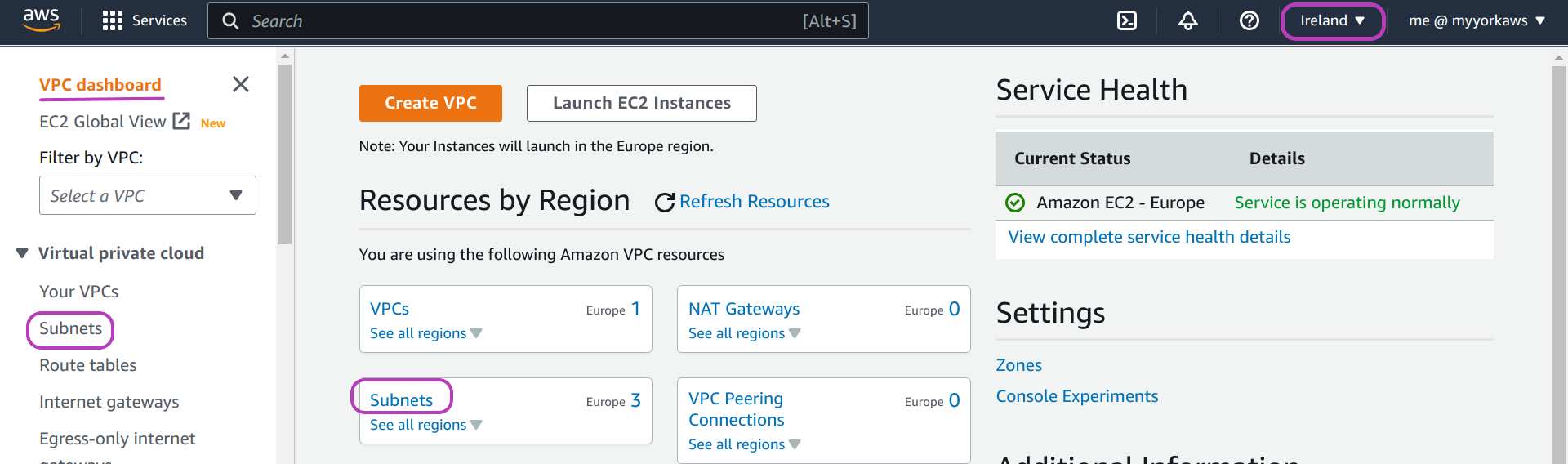
Choose a subnet and make a note of its subnet-id
In the page that appears, “Subnets”, you will see the three subnets available in the Ireland region. Choose one and make a note of its subnet-id as you will use it later to configure the Scripts.